shell脚本加密工具shc
shc是一个加密shell脚本的工具.它的作用是把shell脚本转换为一个可执行的二进制文件.
应用场景
用shell脚本对系统进行自动化维护,简单,便捷而且可移植性好.但shell脚本是可读写的,很有可能会泄露敏感信息,如用户名,密码,路径,IP等.
对于脚本中含有一些敏感信息的,通常我们都想做成二进制程序,不让用户看到源码,对于有这种需求的通常我们一般采用shc或者gzexe,我个人还是比较推荐shc。
shc 安装 和使用
yum -y install shc 或 apt install shc
我们随便写一个脚本
# cat test.sh#!/bin/bashecho \"this is shc test\"
用shc加密
shc -r -v -f test.sh
shc -r -f script-name 注意:要有-r选项, -f 后跟要加密的脚本名.
# ls -ltotal 36-rw-r--r-- 1 root root 37 12月 20 21:48 test.sh-rwx--x--x 1 root root 11160 12月 20 21:48 test.sh.x-rw-r--r-- 1 root root 9433 12月 20 21:48 test.sh.x.c
加密后会生成二个文件
test.sh 源文件
test.sh.x 加密后二进制文件
test.sh.x.c 脚本对应的C语言版本源码
执行一下加密后文件
# ./test.sh.xthis is shc test
shc解密
市面上面现在有对应的unshc解密程序,我们直接去github看看
https://github.com/yanncam/UnSHc/
支持x86 mips arm架构CPU
但对于我测试结果对于x86支持应该是最好的,作者自己维护的,其它的是第三方个人维护,兼容性不好。
# ./unshc.sh /tmp/test.sh.x -o test.txt_ _ _____ _ _| | | | / ___| | | || | | |_ __ \\ `--.| |_| | ___| | | | \'_ \\ `--. \\ _ |/ __|| |_| | | | /\\__/ / | | | (__\\___/|_| |_\\____/\\_| |_/\\___|--- UnSHc - The shc decrypter.--- Version: 0.8------------------------------UnSHc is used to decrypt script encrypted with SHcOriginal idea from Luiz Octavio Duarte (LOD)Updated and modernized by Yann CAM- SHc : [http://www.datsi.fi.upm.es/~frosal/]- UnSHc : [https://www.asafety.fr/unshc-the-shc-decrypter/]------------------------------[*] Input file name to decrypt [/tmp/test.sh.x][+] Output file name specified [test.txt][+] ARC4 address call candidate : [0x400d06][*] Extracting each args address and size for the 14 arc4() calls with address [0x400d06]...[0] Working with var address at offset [0x602179] (0x2a bytes)[1] Working with var address at offset [0x602121] (0x1 bytes)[2] Working with var address at offset [0x602319] (0xa bytes)[3] Working with var address at offset [0x602170] (0x3 bytes)[4] Working with var address at offset [0x6020e0] (0xf bytes)[5] Working with var address at offset [0x602141] (0x1 bytes)[6] Working with var address at offset [0x602127] (0x16 bytes)[7] Working with var address at offset [0x602144] (0x16 bytes)[8] Working with var address at offset [0x60215d] (0x13 bytes)[9] Working with var address at offset [0x6021ad] (0x1 bytes)[10] Working with var address at offset [0x6021ae] (0x1 bytes)[11] Working with var address at offset [0x6020f9] (0x26 bytes)[12] Working with var address at offset [0x6021b3] (0x13 bytes)[13] Working with var address at offset [0x6021c8] (0x13 bytes)[*] Extracting password...[+] PWD address found : [0x6021ec][+] PWD size found : [0x100][*] Executing [/tmp/MYoKED] to decrypt [/tmp/test.sh.x][*] Retrieving initial source code in [test.txt][*] All done!root@Develop:~/UnSHc-master/latest# cat test.txt#!/bin/bashecho \"this is shc test\"
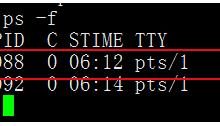
可见直接解密出来源码,对于x86的这种,支持非常的好。 其原理 就是 头部增加4096字节乱码。并且 shc加密的脚本在运行时ps -ef可以看到shell的源码。 因此,shc其实不是真的很有用!
以上就是shell脚本加密工具shc的详细内容,更多关于shell脚本加密工具的资料请关注脚本之家其它相关文章!
您可能感兴趣的文章:
- 使用shc工具加密shell脚本详解
- Powershell实现加密解密文本文件方法实例
- CentOS下对shell脚本加密的二种方法
- 对Shell 脚本加密的方法
- asp木马代码解密的随机加密webshell
 爱站程序员基地
爱站程序员基地